I’m one of those people who heads for the shadows when “fun group activities” are afoot. While I imagine fun ways I could participate, I simply don’t. So when it was announced that this year’s winter-festival-of-your-choice party at work would include a gingerbread house decorating contest, I immediately decided that I would not be participating.
But… I had an idea. I’m one of the only engineers in my group, and I started to think about how a gingerbread house could be expressed abstractly, the way it would look in software. I got some pretty grand ideas.
Still, when the contest organizers were patrolling the area, trying to get people to accept the kit and commit to participating, I demurred. My arm was not twisted. For the next half-hour I heard other arms being twisted, and a loud-for-the-workplace lament that not enough people were participating. “I’ll do it!” I called across the office. “Bring me a kit.” [“Feel the wrath of the arm not twisted!” I didn’t add.]
The kit included a fully-assembled gingerbread house and stuff to stick to it. But in software, that’s not what a house looks like. So my first task was to break the house down to its constituent parts, the same way a software engineer breaks a big problem down into a set of smaller, more manageable problems.

It’s important to recognize here that the front of the house and the back of the house are the same, except for location and orientation. So in software, we define an end panel that works for both cases. Same with the sides, and for the roof panels. You break a thing down into its fundamental pieces, find what’s common between those pieces, and build your structure.
The challenge then, was to present those pieces in a meaningful way, and then create a language that would express how the parts were assembled and how they were decorated. When thoughts of poured-sugar virtual building elements with the parameters that defined them entombed inside gave way to reality, this is where I went:

On a cookie sheet I staged visual representations of the various parts of the house. I included things like the color sequence of the gumdrops when used in series (a co-worker gave me a demerit for not following the Apple rainbow in my sequence. I should have thought of that.) Then there was the purely abstract assembly instructions. The final result looked like this:

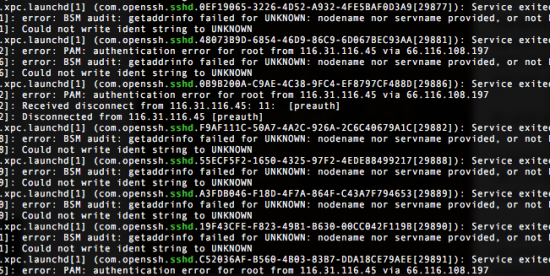
But it’s not software without bugs, and the wreath that came in the kit was broken. I filed the error in the company’s bug-tracking system:
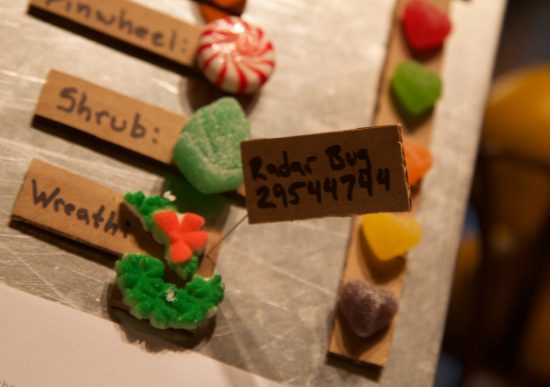
Did I win? No. Of course not. Did I give my co-workers a little insight into how I think? I’d like to think so. I’m surrounded by creative people who view what I do as vaguely magic. Perhaps they understand me a little better now. Though to be honest it would take much more effort than one is likely to give at a holiday party to understand the intricacies of my gingerbread house.

Then there was this conversation:
Me: I think I overdid the roof.
Guy I work with, squinting at my display: Oh?
Me: Piping and a gumdrop on every roof tile? Along with the candies all around the edge. It might be a bit much.
Guy: Where?
Me: It’s all there if you look, but you can only see it in your head.
Guy: Oooh.
And that is my job. I build things you can only see in your head.
 3
3
Sharing improves humanity:






 This episode took a while to get out; there were several things working against it. November was a big one, but this episode resisted me every step of the way all on its own. Then in the middle of the night I figured out what was missing, tied things up, deferred a chunk of exposition to a later date, and here we are!
This episode took a while to get out; there were several things working against it. November was a big one, but this episode resisted me every step of the way all on its own. Then in the middle of the night I figured out what was missing, tied things up, deferred a chunk of exposition to a later date, and here we are!